A Practical Introduction to Subnetting
Learn about IP addresses, Subnet Masks, CIDR, and more
 Imagine living in a sprawling city where the houses are not numbered in any particular order, and you're trying to find your friend's house among a thousand others. Without a map or organization, you'd have to knock on each door or call each house, one by one, every time you wanted to visit. Not only would this take forever, but it would also be a massive waste of energy for both you and the city's residents.
Imagine living in a sprawling city where the houses are not numbered in any particular order, and you're trying to find your friend's house among a thousand others. Without a map or organization, you'd have to knock on each door or call each house, one by one, every time you wanted to visit. Not only would this take forever, but it would also be a massive waste of energy for both you and the city's residents.
This is where subnetting comes in. It's like breaking down the city into well-labeled neighborhoods. Within each neighborhood, houses follow a sequence, and everyone knows which part of the city they're in. This system saves time and confusion, letting messages find the right destination quickly and without bothering the whole city.
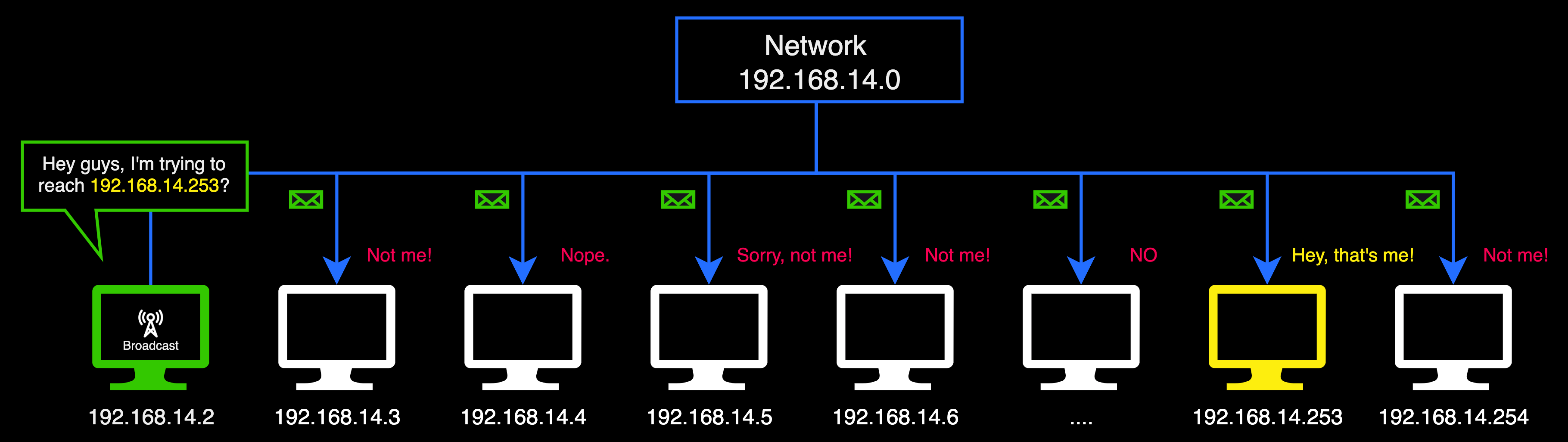 In a network, when a computer wants to locate another computer, it sends a broadcast. The message goes out to EVERY computer on the network to find the specific one it's trying to reach.
In a network, when a computer wants to locate another computer, it sends a broadcast. The message goes out to EVERY computer on the network to find the specific one it's trying to reach.
Imagine if every computer on the network started doing this simultaneously. The network would become incredibly congested, similar to everyone in a room shouting at once. This could lead to a halt due to the overwhelming traffic created by all these computers trying to communicate at the same time.
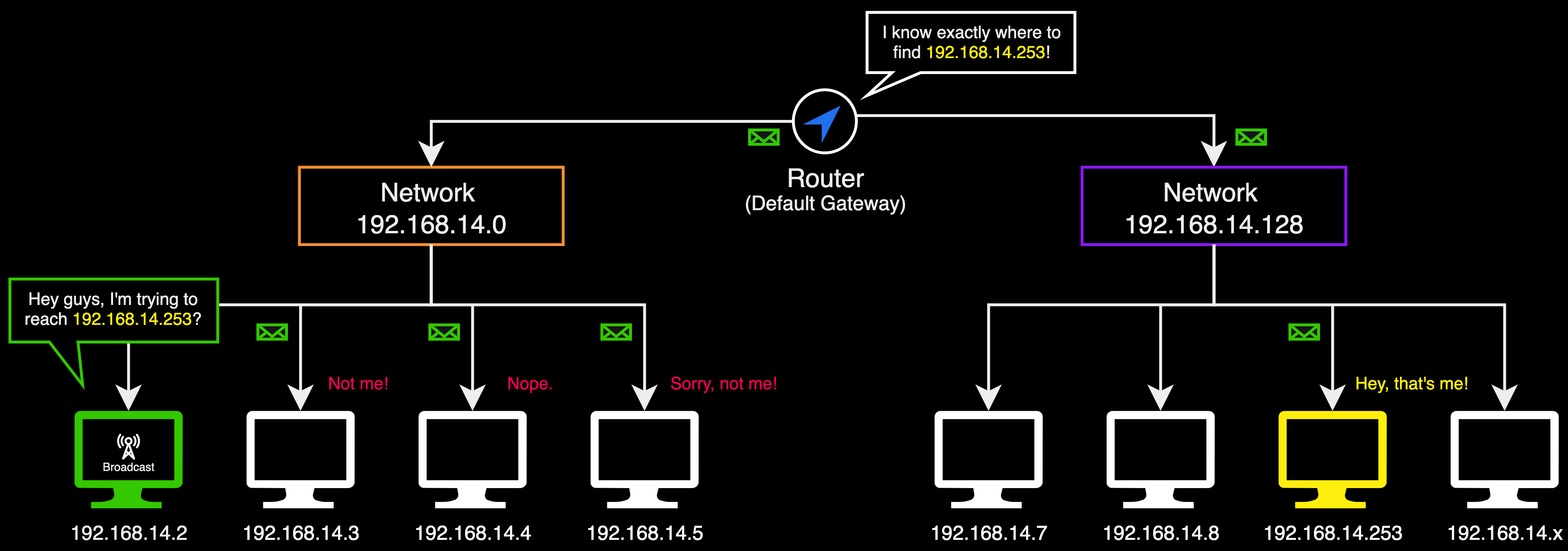 To prevent network congestion, networks are divided into smaller segments using routers. A router is a device that directs data traffic between different networks, ensuring that information reaches its intended destination. These routers act as barriers that contain broadcasts within their respective segments, ensuring that the communication does not overflow into other parts of the network.
To prevent network congestion, networks are divided into smaller segments using routers. A router is a device that directs data traffic between different networks, ensuring that information reaches its intended destination. These routers act as barriers that contain broadcasts within their respective segments, ensuring that the communication does not overflow into other parts of the network.
The Internet Protocol
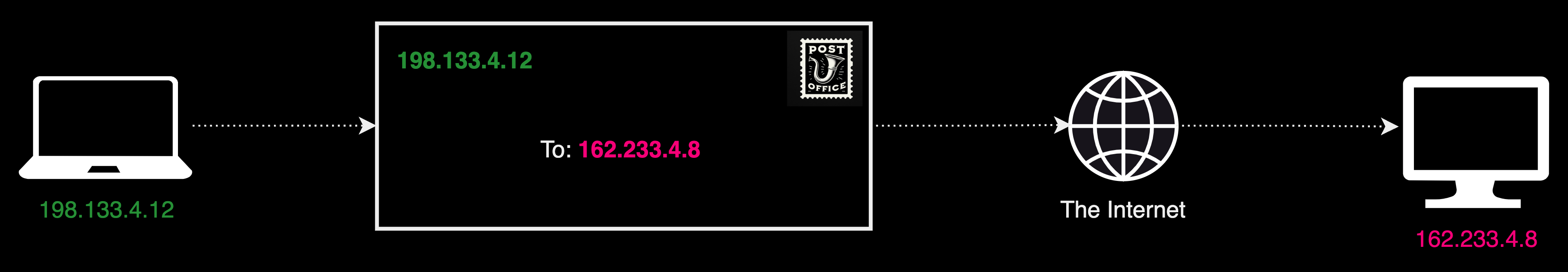 The Internet Protocol is the backbone system of internet communication. The IP refers to a set of rules governing how data should be formatted, addressed, transmitted, routed, and received across a network.
The Internet Protocol is the backbone system of internet communication. The IP refers to a set of rules governing how data should be formatted, addressed, transmitted, routed, and received across a network.
Continuing with the analogy of a city, envision the Internet Protocol as the digital counterpart to a city's postal system. Just as postal addresses on an envelope guide mail to the correct house, IP addresses in the Internet Protocol ensure that data is directed to the right place in the internet.
IP Addresses
To ensure data packets arrive at the right destination, every device connected to the internet receives a unique identifier called an IP address. While there are two types of IP addresses - IPv4 and IPv6 - this article primarily discusses IPv4 addresses.
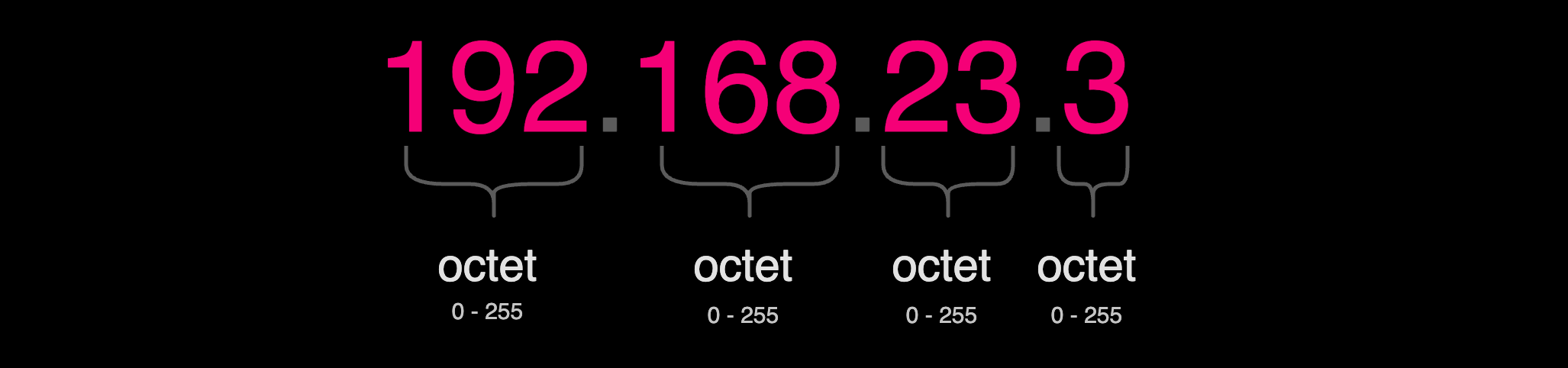 An IPv4 address consists of four sets of numbers, known as octets, separated by dots. Each octet ranges from 0 to 255 and comprises 8 bits, bringing the total to 32 bits for the entire IP address. A bit is simply a digit that can be either a 1 or a 0. You're probably able to recognize an IP address in the format
An IPv4 address consists of four sets of numbers, known as octets, separated by dots. Each octet ranges from 0 to 255 and comprises 8 bits, bringing the total to 32 bits for the entire IP address. A bit is simply a digit that can be either a 1 or a 0. You're probably able to recognize an IP address in the format 192.168.23.3. However, to a computer it actually looks like this 11000000.10101000.00010111.00000011.
In other words, and IP address is simply a unique combination of 32 of 1s and 0s. That means there's a finite number of IPv4 addresses, to be precise, 2 32 which is approximately 4.2 billion addresses. Where 2 represents the two states of the bit (either 1 or 0), and 32 because there are 32 bits in each IP address.
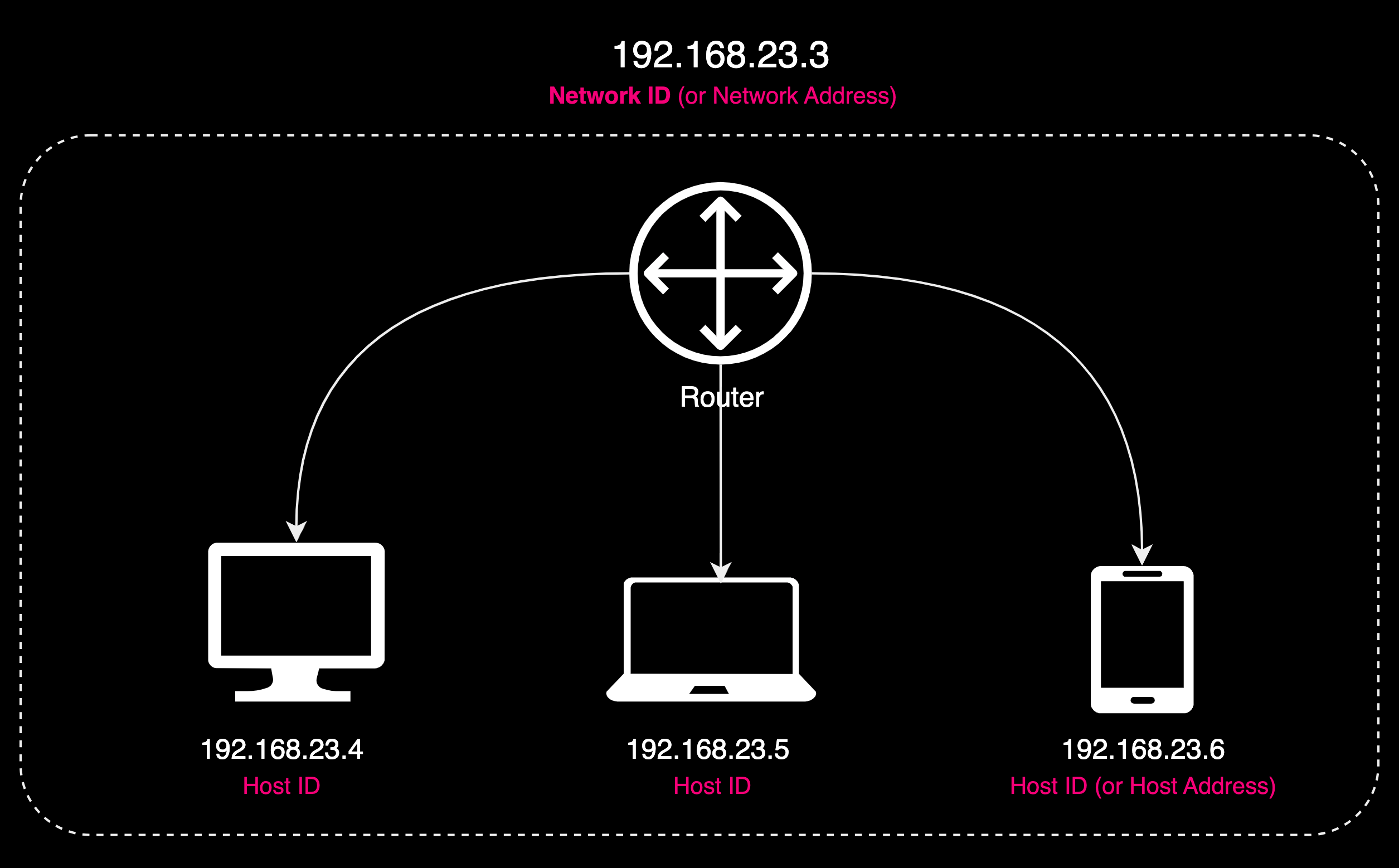 An IP address has two main parts: the network address and the host address. The network address (also known as network ID) uniquely identifies the network, much like the name of a neighborhood, while the host address is similar to a specific house number, assigned to each host (a device) within a network.
An IP address has two main parts: the network address and the host address. The network address (also known as network ID) uniquely identifies the network, much like the name of a neighborhood, while the host address is similar to a specific house number, assigned to each host (a device) within a network.
IP Address Classes
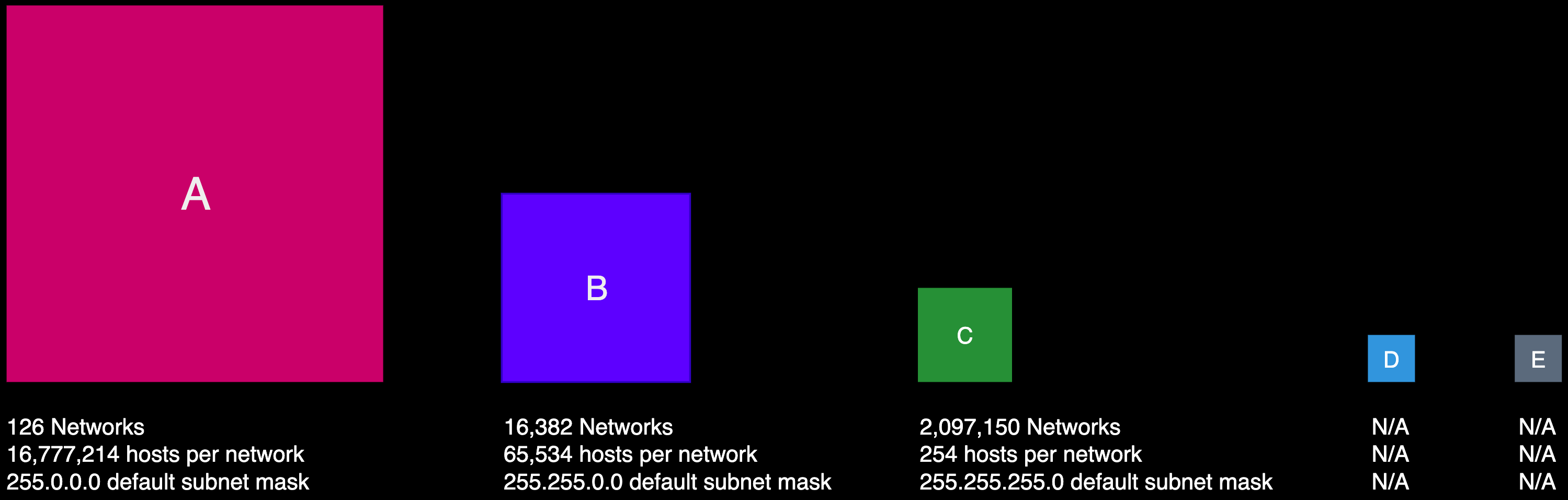
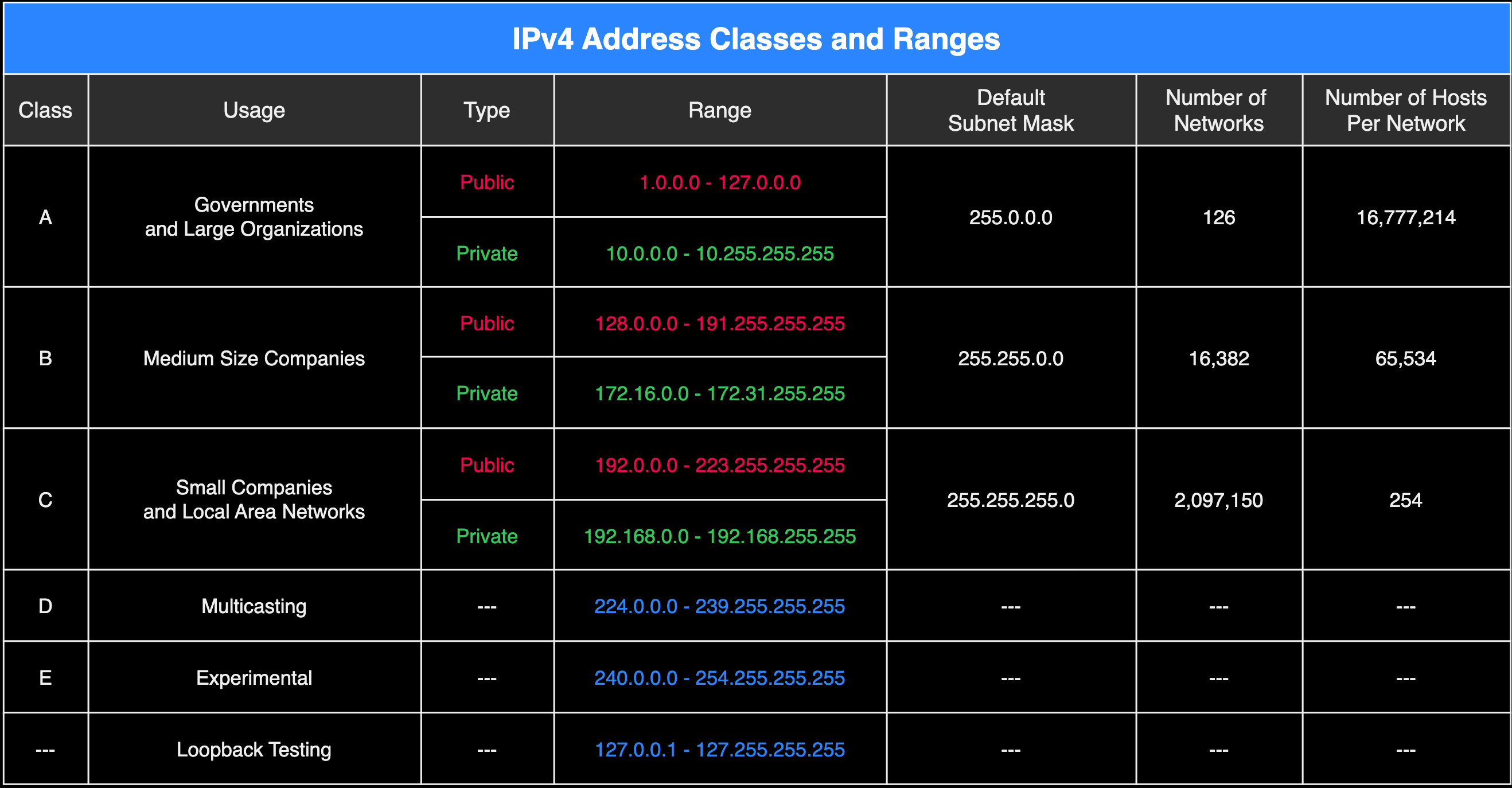
In the early stages of the internet, IPv4 addresses were organized using a method known as classful addressing, introduced in the 1981 document (RFC 791). This system categorized IPv4 addresses into five classes: A, B, C, D, and E. Each class was assigned a default subnet mask. We'll talk more about subnet masks in a moment, but just to give you enough context, a subnet mask is what enables you to identify the network from the hosts in an IP address.
Another interesting aspect of this system is the concept of classless addresses. An IP address is considered classless if its subnet mask does not align with its default network class. For instance, an IP address like 10.8.4.0 coupled with a subnet mask 255.255.255.0 would be an example of a classless address. This distinction reflects a move from rigid class-based structures to more flexible addressing methods which we'll talk about later on when we get to the CIDR section.
The following table summarizes classful addressing and provides you some more relevant information such as public and private IP addresses, as well as their ranges, the number of networks, the number of hosts per network and their intended use.
The Subnet Mask
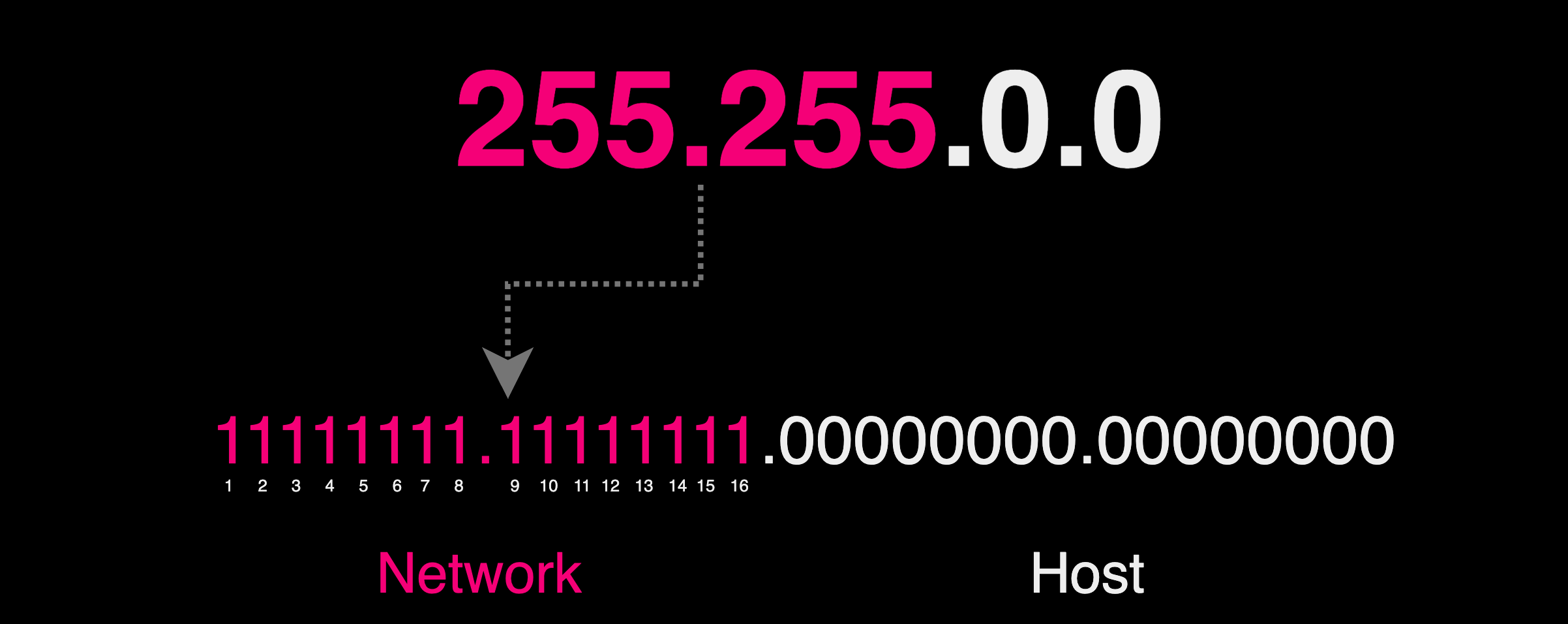 The purpose of a subnet mask is to extract the network ID and the host ID from the IP address. The network bits are matched by the 1s in the mask, and the host bits are matched by the 0s. Subnet masks are usually presented in two forms - dotted decimal notation and CIDR notation.
The purpose of a subnet mask is to extract the network ID and the host ID from the IP address. The network bits are matched by the 1s in the mask, and the host bits are matched by the 0s. Subnet masks are usually presented in two forms - dotted decimal notation and CIDR notation.
A subnet mask, similar to an IP address, is written in decimal form as four groups of numbers, known as octets, separated by dots. For instance, a commonly used subnet mask is 255.255.0.0. In this format, each octet represents a set of 8 bits, making up a total of 32 bits. The subnet mask helps identify which part of an IP address is used for the network and which part for the host (or individual devices on the network).
In the example 255.255.0.0, the 255 in the first two octets translates to binary as 11111111, which means all 8 bits in each of these octets are set to '1'. This indicates that the first 16 bits of the IP address (8 bits x 2 octets = 16 bits) are reserved for identifying the network.
The last octet, 0, translates to 00000000 in binary, meaning all 8 bits are set to '0'. These 8 bits are reserved for identifying individual hosts within the network. Therefore, this subnet mask tells us that the network part of the IP address is defined by the first two octets, and the host part by the last two octets.
Classless Inter-Domain Routing (CIDR)
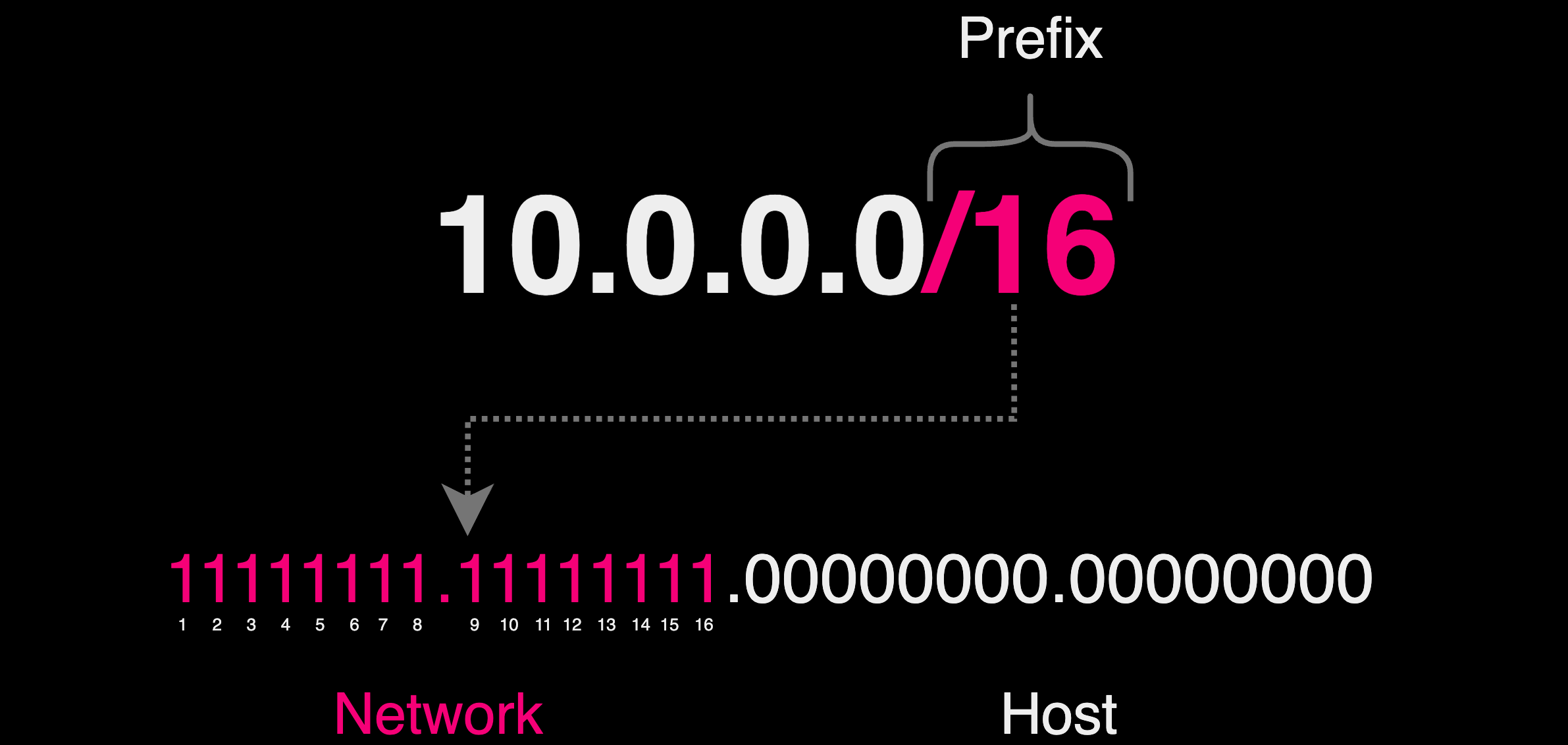
As the internet expanded, the limitations of the classful addressing system became evident, especially with the inefficient allocation of large blocks of IP addresses the Classless Inter-Domain Routing (CIDR) system was created.
CIDR allows for a more flexible and efficient allocation of IP addresses. Under CIDR, any part of an IP address can be used to designate the network or host segment, based on the specified "prefix" length.
A prefix is a part of the IP address that indicates the network portion of the address. It is represented by the number that follows the slash ("/") in the CIDR notation. This number specifies how many bits, counting from the leftmost bit of the address, are used for the network portion. The remaining bits represent the host portion within that network.
For example, in the CIDR notation 192.168.4.0/24:
192.168.4.0is the IP address./24is the prefix.- It means the first
24bits (out of a total of32bits for IPv4 addresses) are used for the network part. - The subnet mask corresponding to a
/24prefix is255.255.255.0, where the first24bits are set to1, and the remaining bits are0.
Private IPv4 addresses to the Rescue
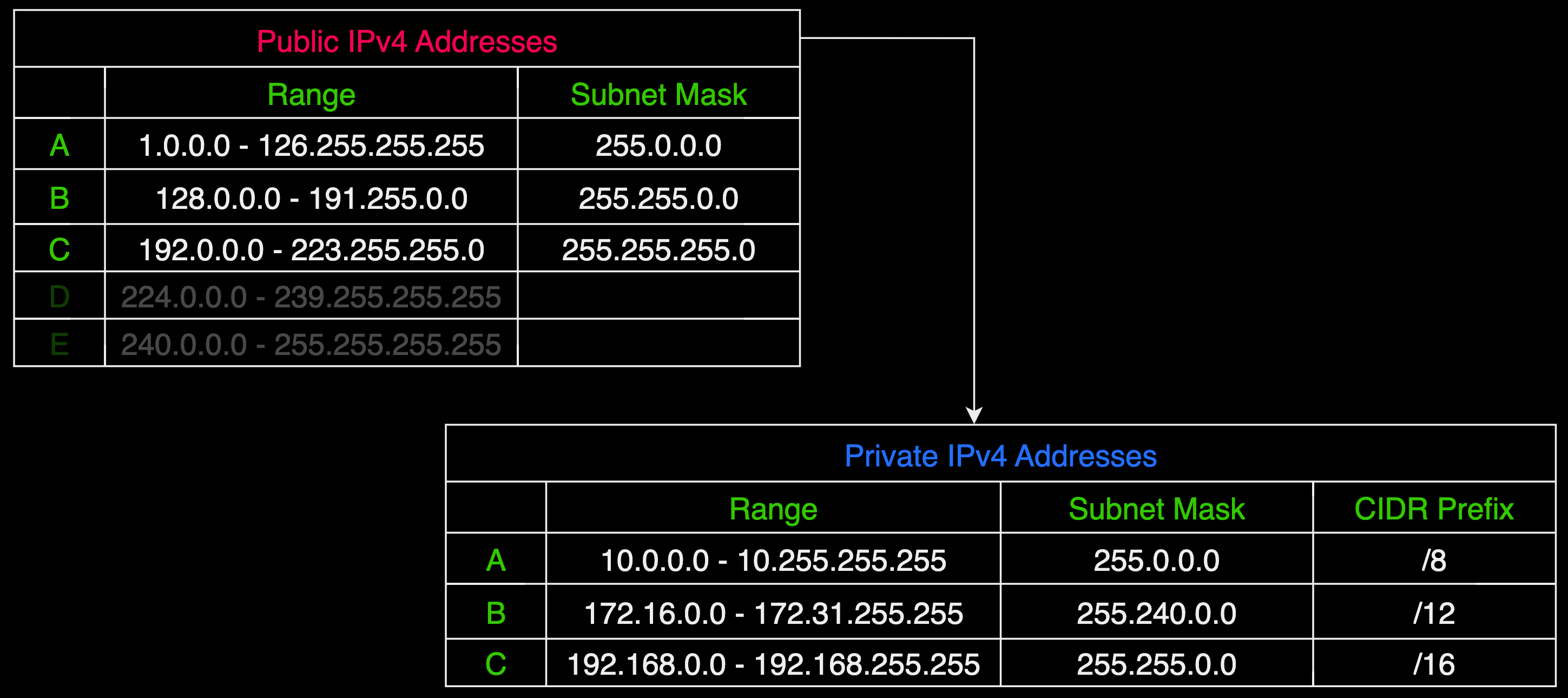
Due to the rapid profiliferation of the internet, IPv4 addresses quickly became scarce. This scarcity was officially recognized by Europe's Regional Internet Registry, RIPE, on November 25, 2019, when it was announced that the pool of available IPv4 addresses had been exhausted.
In response to this impending shortage, the RFC 1918 document, titled "Address Allocation for Private Internets", was introduced in February 1996. This document specified certain ranges of IP addresses to be used exclusively for private networks. These private IP addresses are not routable on the global internet, meaning they are not used for direct internet communication but rather within internal networks.
Network Address Translation (NAT)
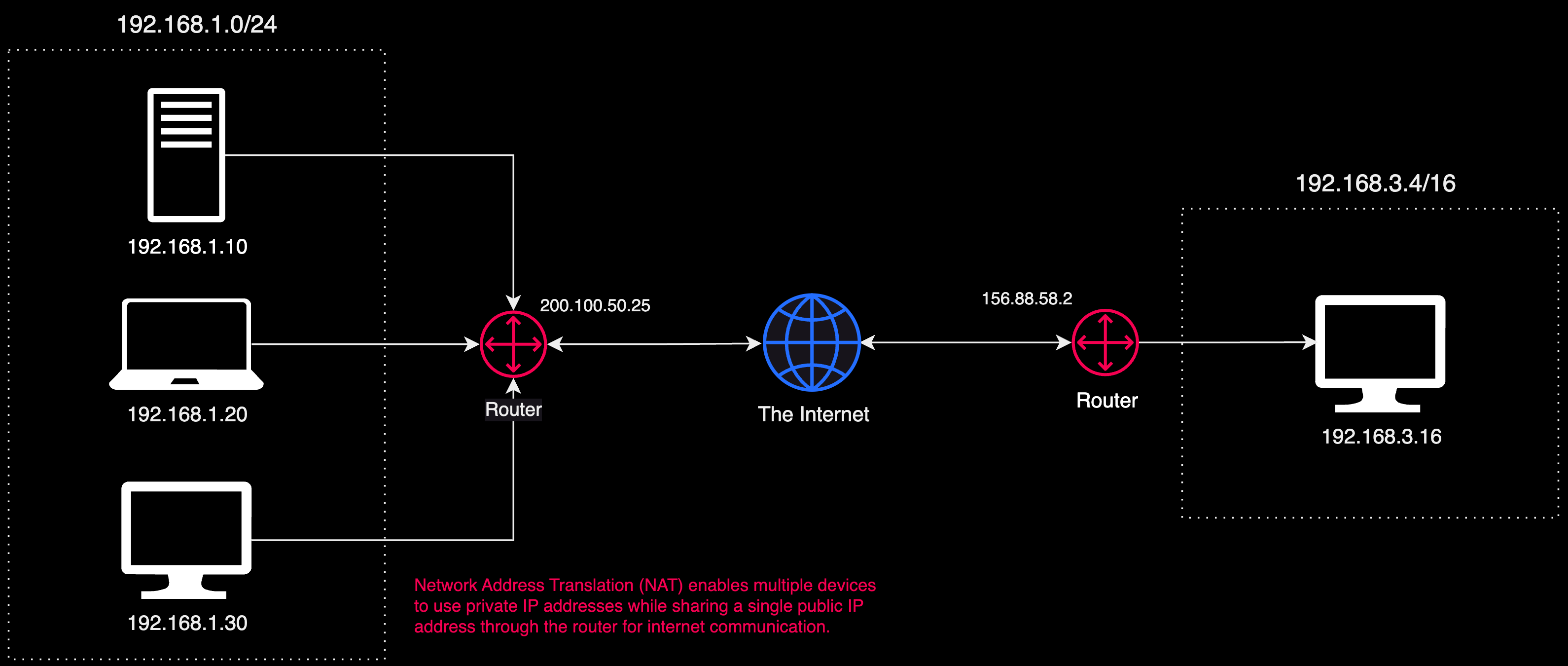 When multiple devices in a local network connect to the internet, they typically use the same public IP address. This is made possible by a process called Network Address Translation (NAT), which is carried out by the router. NAT allows each device on the local network to have its own private IP address, while the router uses a single public IP address to communicate with the internet on behalf of these devices. This setup not only conserves public IP addresses but also adds a layer of security, as individual device IP addresses are not exposed to the internet.
When multiple devices in a local network connect to the internet, they typically use the same public IP address. This is made possible by a process called Network Address Translation (NAT), which is carried out by the router. NAT allows each device on the local network to have its own private IP address, while the router uses a single public IP address to communicate with the internet on behalf of these devices. This setup not only conserves public IP addresses but also adds a layer of security, as individual device IP addresses are not exposed to the internet.
When a device from a private network communicates with the internet, the NAT router substitutes the device's private IP address with its own public IP address. This substitution is tracked using a unique source port number for each session, recorded in a translation table. This tracking is essential for ensuring that responses from the internet are routed back to the correct device on the private network. By using NAT, not only are public IPv4 addresses conserved, but the security of the network is also enhanced, as internal IP addresses remain concealed from external entities.
IPv6 Addresses
 Long before the imminent exhaustion of IPv4 addresses was forcasted. RFC 2460, which was titled "Internet Protocol, Version 6 (IPv6) Specification," was introduced in December 1998, and more recently RFC 8200 in July 2017. In essence, this new architecture would allow us to never ever run out of IP addresses.
Long before the imminent exhaustion of IPv4 addresses was forcasted. RFC 2460, which was titled "Internet Protocol, Version 6 (IPv6) Specification," was introduced in December 1998, and more recently RFC 8200 in July 2017. In essence, this new architecture would allow us to never ever run out of IP addresses.
IPv6 uses 128-bit addresses, which allows for 2128 possible addresses. This number is approximately 3.4 x 10 38, or 340 undecillion addresses. This vast address space was designed to provide a practically inexhaustible supply of unique IP addresses, avoiding the limitations encountered with the 32-bit address space of IPv4.
Subnetting Math
Before you get started with subnetting, you have to understand some basic subnetting math such as converting octets to binary, and calculating the network address.
Converting Octets to Binary
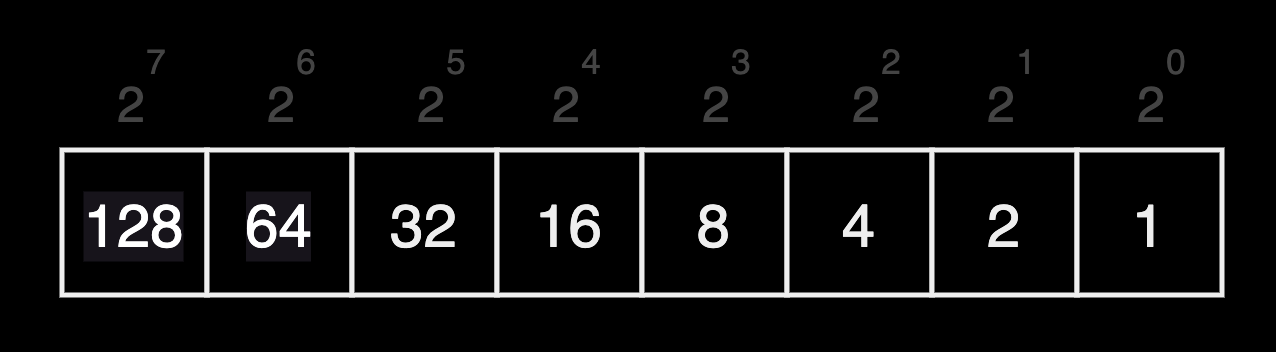 To convert an IP address octet to binary, you use an 8-bit octet table. This table allows you to determine which part of the IP address is for the network and which part is for hosts, you compare the binary form of the IP address to the network mask using the AND bitwise operation.
To convert an IP address octet to binary, you use an 8-bit octet table. This table allows you to determine which part of the IP address is for the network and which part is for hosts, you compare the binary form of the IP address to the network mask using the AND bitwise operation.
This means you look at the bits in the same position in both the IP address and the network mask: if both are 1, you write down 1; if either or both are 0, you write down 0. The result shows which part of the IP address refers to the network. Remember that the 1s indicate the bits reserved for the network, and the 0s indicate the bits reserved for the hosts.
Example 1
Let's take a look at a simple example using the IP address 192.168.4.0 with a subnet mask of 255.255.254.0.
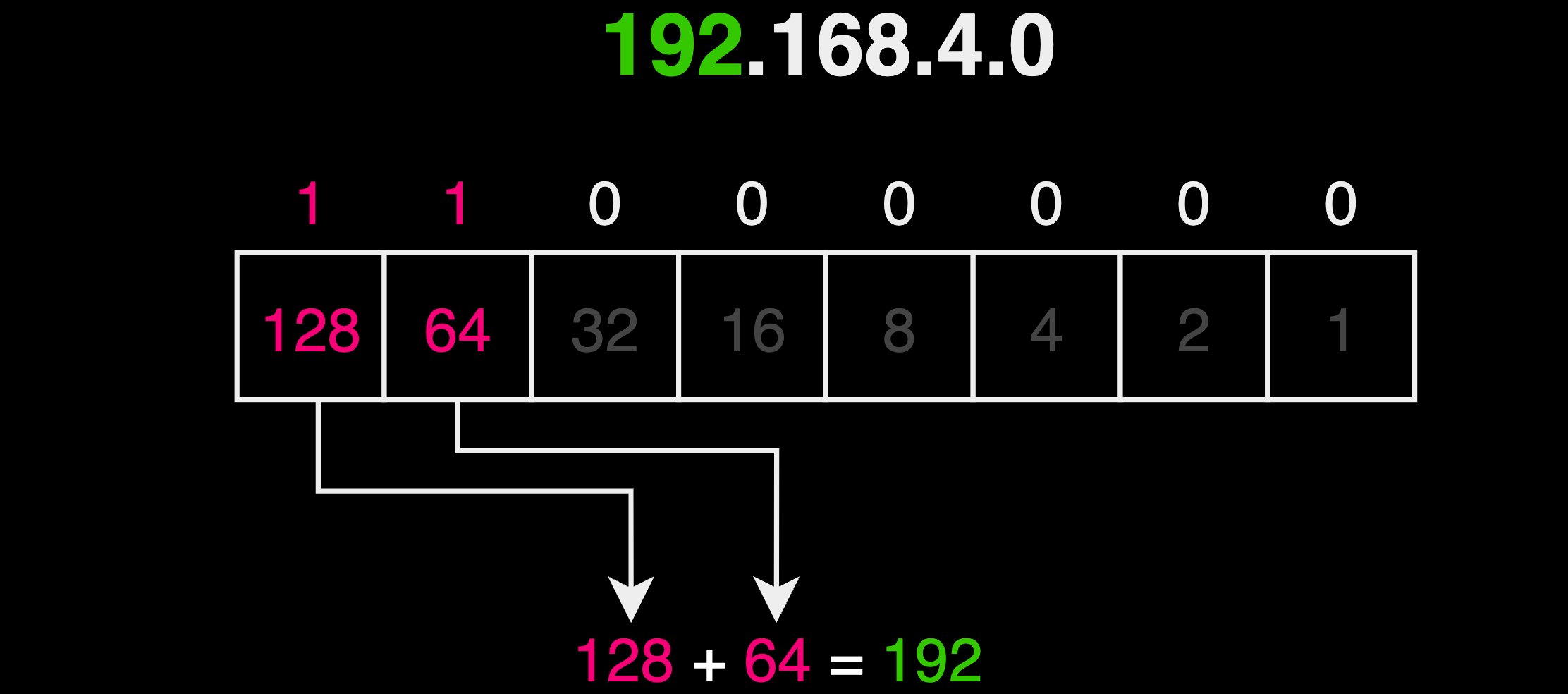
- To create an 8-bit octet chart, list eight numbers starting with 128, which is 2 raised to the power of 7. Then, successively divide by 2 as you move to the right, resulting in: 128, 64, 32, 16, 8, 4, 2, 1. Each number corresponds to a bit in the octet, from left to right.
- Find the first octet of the IP address; here it is
192. - Under the octet chart, place a
1beneath each number that, when added together, equals192. In this case, it's the first two numbers: 128 and 64, because128 + 64 = 192. - Under the octet chart, place a 0 beneath each of the remaining numbers.
- Now, read off the
1s and0s beneath the octet chart from left to right to form the binary number. - The resulting binary number should be
11000000, which is the binary equivalent of the decimal number192.
We repeat the same process for the remaining octets in the IP address:
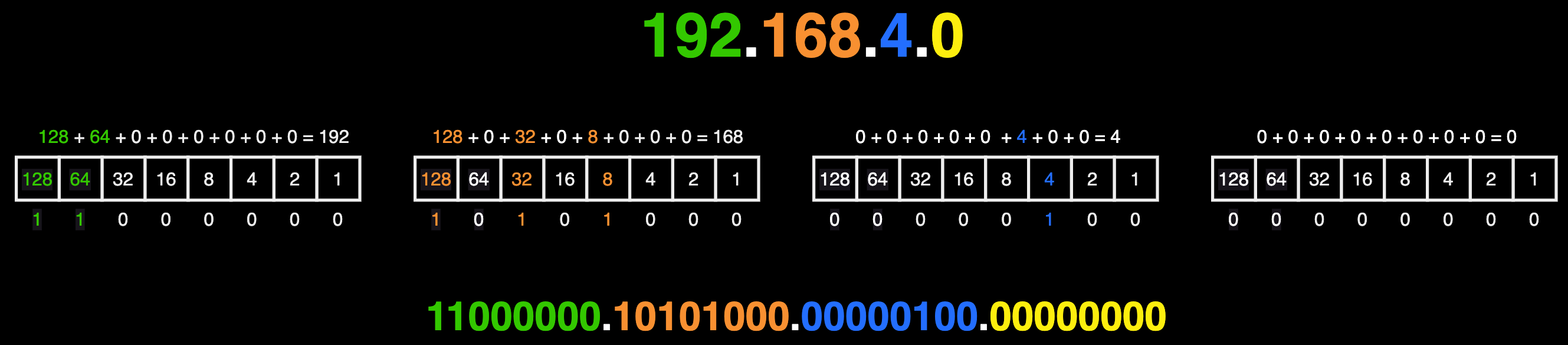
As you can see, 11000000.10101000.00000100.00000000 is resulting binary notation for 192.168.4.0.
Then, you follow the same process for the subnet mask, 255.255.254.0:
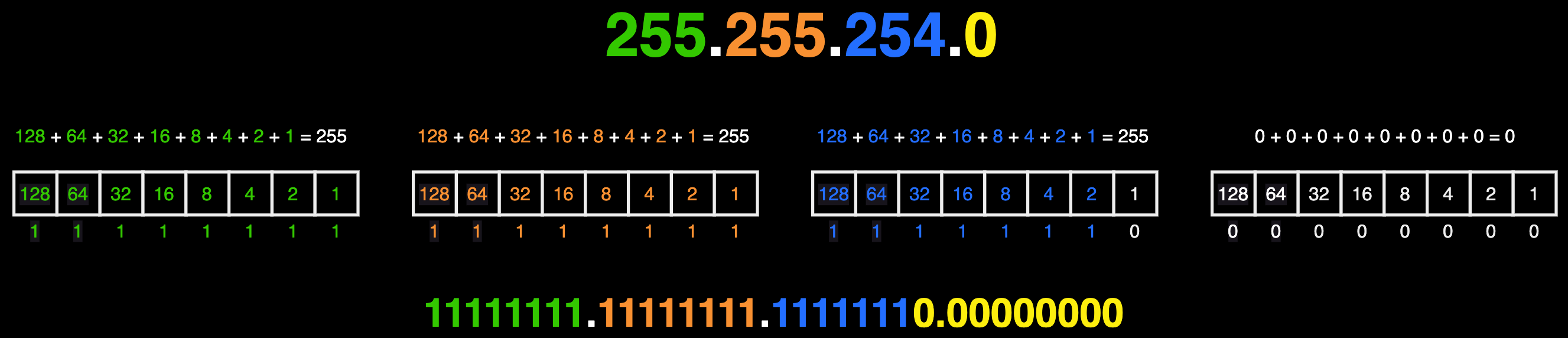
Next we can find the number of bits that are for the network and the number of bits that are for the hosts. We do this by crossing out all the digits in the IP address binary that line up with the 1s in the the network mask:

As you can see, the first 23 bits are allocated for the network, and then remaining 9 bits are for hosts.

Extracting Subnetting Information
Now that we know how many bits are allocated for the network and which bits are allocated for hosts, we can extract 7 important pieces of information - The CIDR prefix, the number of IP addresses, the Network ID, the first host IP, the last host IP, the broadcast address, and the next network.
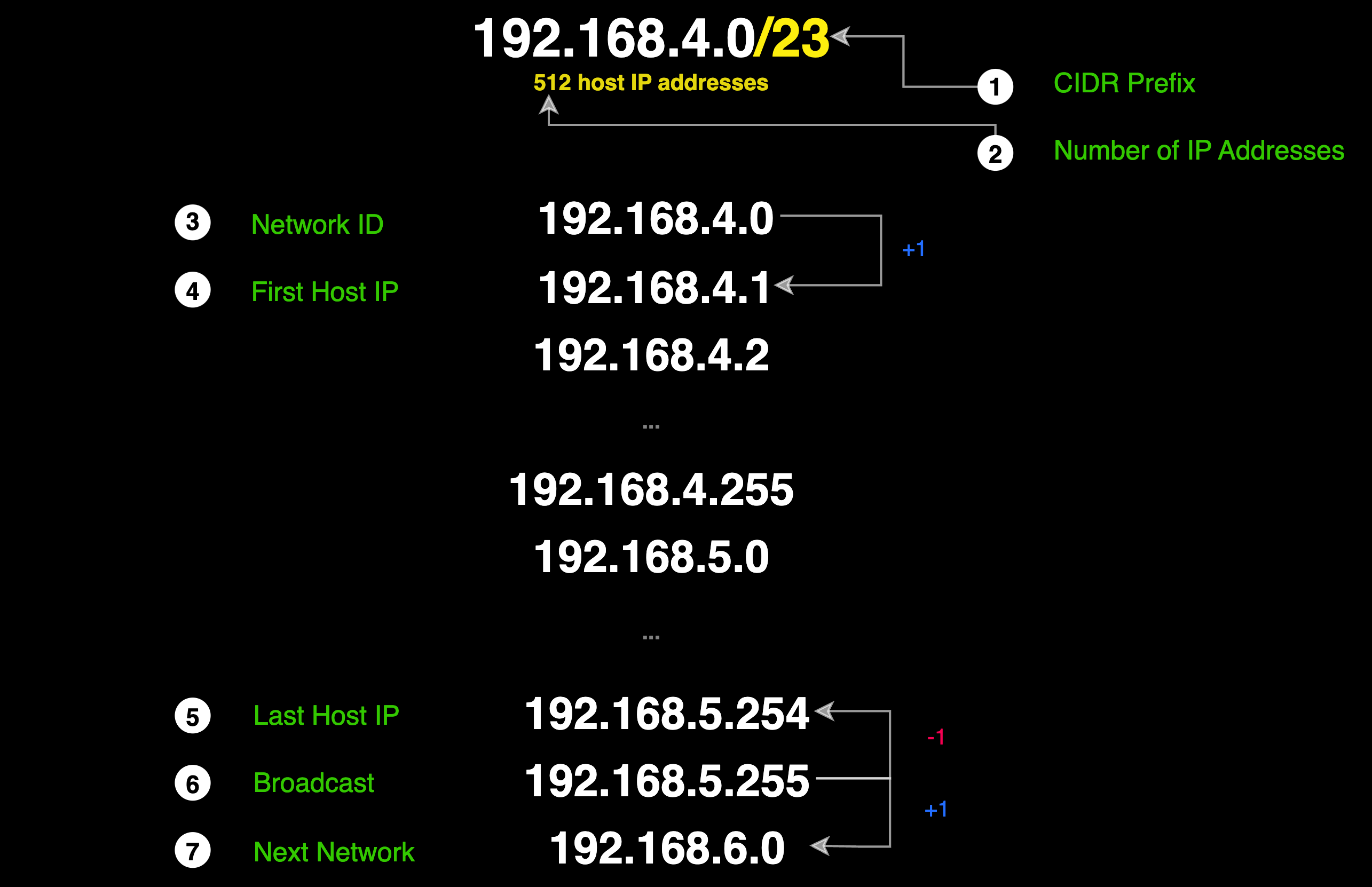
The CIDR Prefix/Subnet Mask
The subnet mask 255.255.254.0 in binary is 11111111.11111111.11111110.00000000. The CIDR prefix is the number of 1s in the subnet mask, which in this case is 23 (since there are 23 consecutive 1s before the first 0). Therefore, the CIDR notation for the given IP address and subnet mask is 192.168.4.0/23.
Number of IP Addresses
With a /23 subnet mask (or 255.255.254.0), there are 232 - CIDR prefix = 232 - 23 = 29 = 512 IP adresses in total.
Alternatively, you can calculate the total number of IP addresses by counting the number of 0s and raising 2 to the power of that value. For example. 2 number of 0s = 512
The number of usable IP addresses is 512 minus 2 (one for the network address and one for the broadcast address), so that leaves 510 usable IP addresses.
The Network Address
We found the network address when we performed the bitwise AND operation on the binary representation of the IP address and the subnet mask.
You can say that the network address is always the first IP address in an IP range of a particular network. This address is used to identify the network itself and is derived based on the subnet mask associated with the IP range.
Therefore, the IP block 192.168.4.0/23 the Network address is 192.168.4.0.
The First Host IP
The first host IP is the network address plus one in the host portion. Therefore, the first host IP is 192.168.4.1.
Broadcast Address
The broadcast address is the last address in the IP block. It's used for sending data to all devices in this subnet.
For the network 192.168.4.0/23, which consists of 512 IP addresses, the calculation of the broadcast address can be understood as follows: Starting from the network address 192.168.4.0, you first consider the first block of 256 addresses.
Adding 255 to the network address (since the range starts at 0), you reach 192.168.4.255, which is the end of the first 256-address block. The next address, 192.168.5.0, marks the beginning of the second block of 256 addresses. As 192.168.5.0 is counted as the first address in this block, adding 255 to it (again, counting from 0) leads you to 192.168.5.255. This address is the last in the 192.168.4.0/23 subnet range and is designated as the broadcast address.
The Last Host IP
The last host IP is one less than the broadcast address. Therefore, the last host IP is 192.168.5.255 - 0.0.0.1 = 192.168.5.254.
The Next Network:
The next network is found by adding 1 more IP to the broadcast address. Therefore, 192.168.5.255 + 0.0.0.1 = 192.168.6.0.
Solving Subnetting Problems
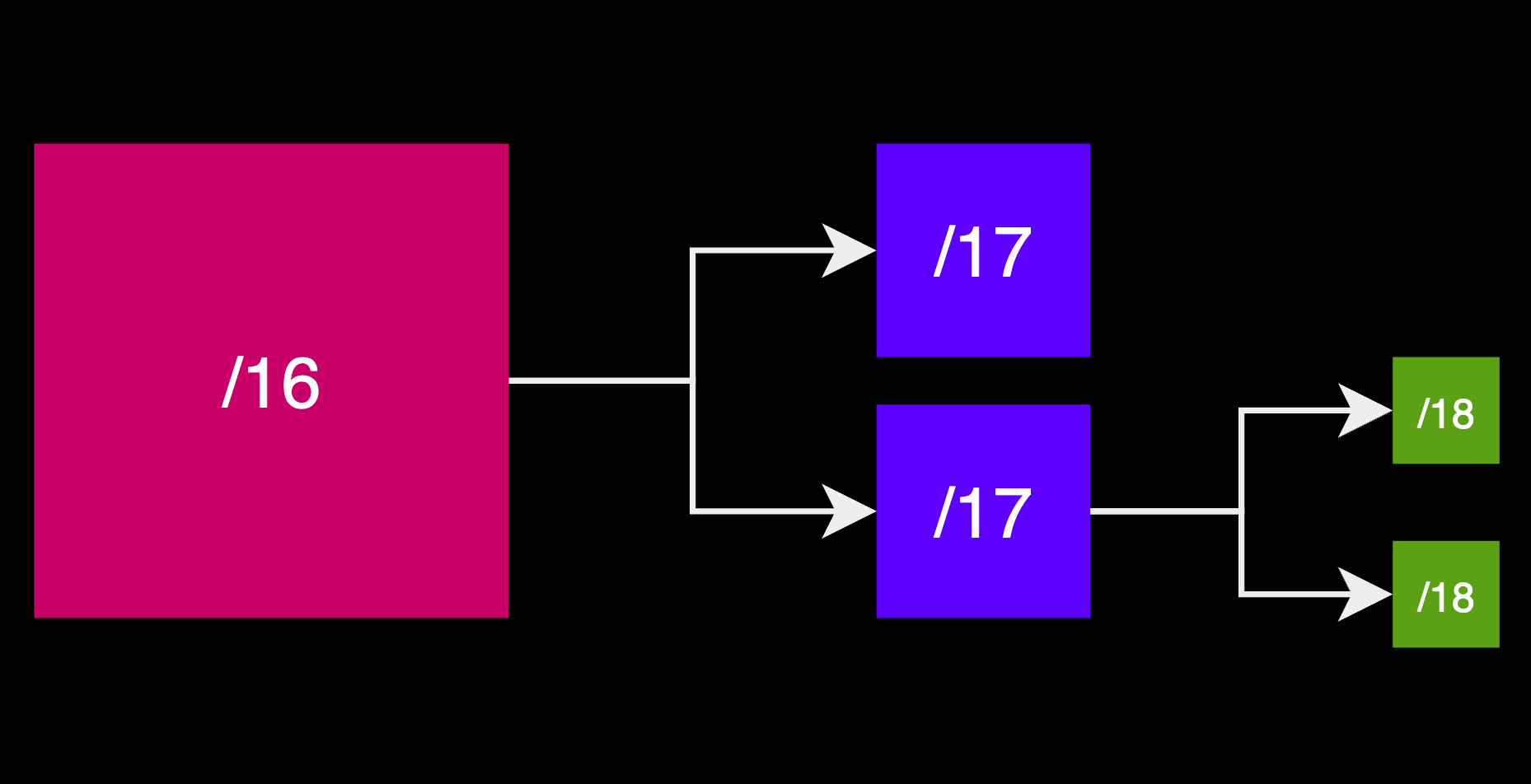
Subnetting in IP networking simplifies managing large networks by dividing them into smaller, more manageable subnets. This is done by adjusting the subnet mask, which defines the division between the network portion (identifying the specific network) and the host portion (identifying a specific device within the network) of an IP address.
By altering the subnet mask and reallocating or "borrowing" bits from the host portion, we extend the network portion, creating additional subnets.
The Subnetting Process
The subnetting process consists of 4 steps:
- Subnet Sizing: Determine how many bits you'll need for your new subnetworks.
- Borrowing Host bits: Use binary notation to borrow host bits, and generate a new subnet mask.
- Finding the Increment: Calculate the number that will be used figure out the different subnet ranges.
- Calculating Subnet Ranges: Identify all the new subnets ranges generated.
Subnet Sizing: how many bits do we need?
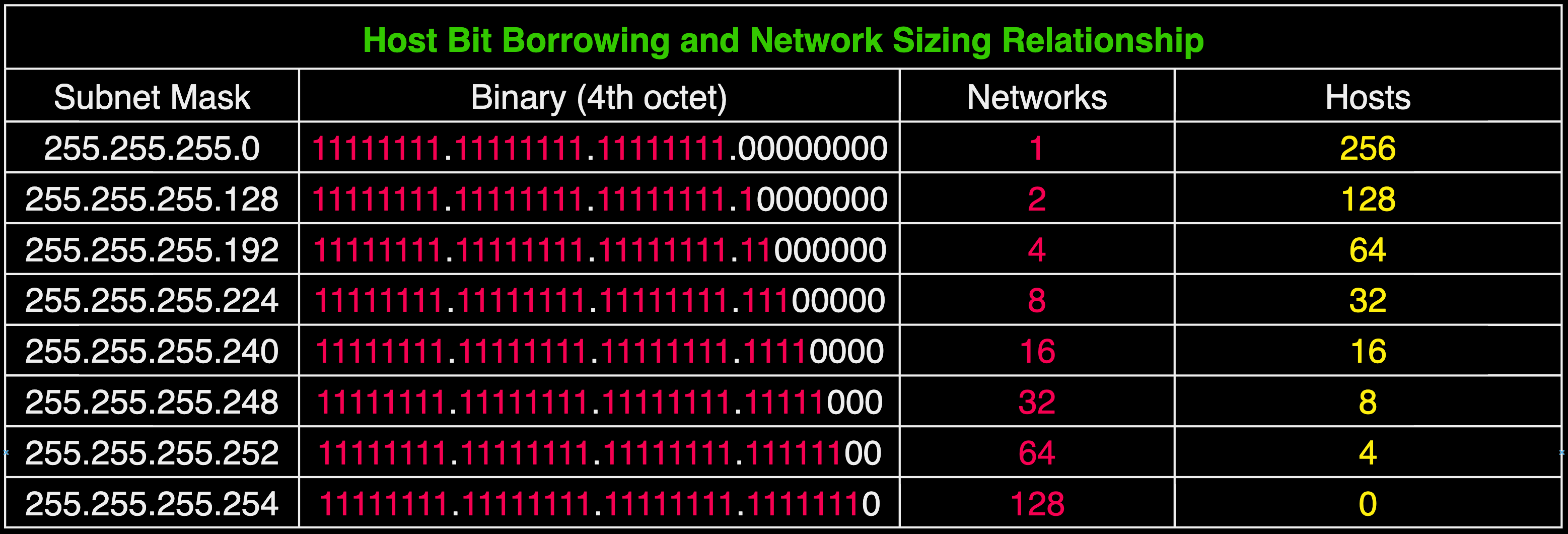
The table above demonstrates the relationship between borrowing bits, and the number of networks that are created. The more bits that the network portion borrows from the host portion, the amount of networks that can be created also doubles.
Imagine you got a requirement to generate 4 subnets with 120 hosts each.
Well, according to our chart. If we need 4 subnets, then we need to borrow a total of 2 bits. That's because with every bit we borrow, the size of the subnet is split in half, along with the number of hosts in that subnet.
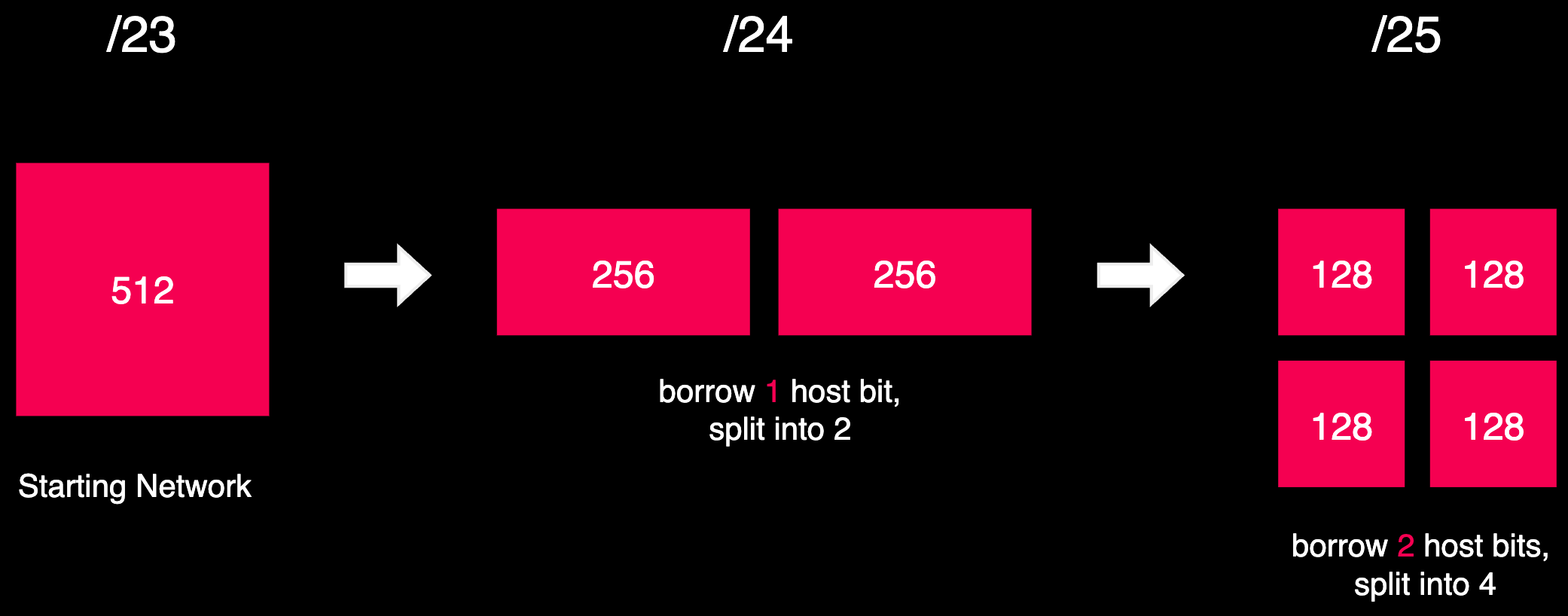
🙋♂️ Question
What if the requirement was 3 subnets, with 170 addresses each? After all we have 512 addresses at our disposal. We could just divide 512 by 3, right? Would that be possible?
In short, no.
IP addressing and subnetting are fundamentally binary, meaning they operate based on powers of two. This is because each bit in an IP address can be either 0 or 1, and subnetting involves manipulating these bits.
The size of each subnet, therefore, must align with powers of two (e.g., 2, 4, 8, 16, 32, etc.). This is due to how binary numbers scale and how IP addresses are structured.
Because subnet sizes must follow powers of two, you can create 2, 4, 8, etc., subnets, but not 3. There's no combination of binary bits that can be turned on or off to create exactly three evenly sized subnets.
For example, with one bit for subnetting, you create two subnets; with two bits, you create four subnets. There's no way to allocate bits to create exactly three subnets.
When you have a requirement that doesn't fit into the powers-of-two structure, such as needing three subnets, you have to choose the next highest power of two (which would be four in this case) and accept that there will be an additional unused subnet.
Borrowing Host Bits
In the Subnetting Math section, we used
192.168.4.0/23(255.255.254.0) as an example, we'll continue using it throughout the next few steps.
We start with the subnet mask 255.255.254.0. In binary, this is 11111111.11111111.11111110.00000000. We plan to modify ("borrow") 2 bits in this subnet mask to create more subnets.
By changing the last '0' of the third octet and the first '0' of the fourth octet to '1's, our subnet mask in binary becomes 11111111.11111111.11111111.10000000. Translated into decimal form, this new subnet mask is 255.255.255.128. This change means we've effectively borrowed two bits from the host portion to extend the network portion, shifting from a /23 to a /25 subnet.
Next, let's align the binary representation of an IP address with this new subnet mask:
11000000.10101000.00000100.00000000 (IP Address - 192.168.4.0)
11111111.11111111.11111111.10000000 (New Subnet Mask - 255.255.255.128)
Applying the new subnet mask to the IP address, we determine the network address. Since the new mask still allows the first three octets of the IP address to be part of the network address, the new network address remains as 192.168.4.0 (11000000.10101000.00000100.00000000 in binary).
That makes our new CIDR block 192.168.5.0/25.
Finding The Increment
In subnetting, once we've adjusted the subnet mask, the next crucial step is to determine the "increment." This is essentially the size of each subnet and the number of addresses within it. To find the increment, we look at the last network bit in the subnet mask's binary representation.
Think of the increment as the step size for each subnet; it's given by the value of the rightmost '1' bit in the binary form of the subnet mask.
For instance, in the subnet mask 255.255.255.128 (binary 11111111.11111111.11111111. 👉 1 👈 0000000), the rightmost '1' corresponds to 128. This means each subnet will encompass 128 IP addresses, including both the network and broadcast addresses.
Calculating Subnet Ranges
To calculate subnet ranges, begin with your initial network address. For us, that is 192.168.4.0, paired with a subnet mask like 255.255.255.128. This combination yields an increment of 128.
The first subnet starts at your network's initial address, in our example, 192.168.4.0. It extends to 192.168.4.127. This range is derived from the increment of 128, meaning the subnet includes 128 addresses, starting from 0. Therefore, the range covers addresses from 192.168.4.0 up to 192.168.4.127.
The subsequent subnet begins immediately after the last address of the previous one. In this scenario, the next subnet starts at 192.168.4.128, following the end address 192.168.4.127 of the first subnet. It extends up to 192.168.4.255, also spanning 128 addresses, following the established increment. This pattern is repeated for each additional subnet you need to calculate.
At the end we get the following subnet ranges:
192.168.4.0-192.168.4.127192.168.4.128-192.168.4.255192.168.5.0-192.168.5.127192.168.5.128-192.168.5.255
Conclusion
Subnetting is a crucial skill in networking and in many other areas of Computer Science. In this article, we explored the concept by drawing parallels with organizing a sprawling city into smaller segments. The journey covered various aspects, including the Internet Protocol, IP addresses, their classification, Classless Inter-Domain Routing (CIDR), Network Address Translation (NAT), and converting octets to binary. We delved into subnet masks, extracting essential subnetting information, and the technique of dividing a large network into smaller, more manageable subnets by borrowing host bits.
Thank you for reading this far. This article reflects my current understanding of subnetting, developed through extensive reading and watching videos. Networking is not my primary area of expertise, so I am open to suggestions and constructive criticism. Please feel free to reach out with your thoughts. Happy learning, and I hope you found this article helpful!